Spring Security is one of the Spring team's products that have been implemented using the Spring framework for Java.
Spring Security is a powerful and highly customizable framework designed to secure Java applications. It has built-in authentication, authorization, and other security features with minimal configuration.
Why Do We Need Spring Security?
When you open your application to the public, you are exposing it to malicious actors who will attempt to exploit it.
Without security, attackers can:
- Log in with stolen credentials
- Access Restricted data
- Delete or alter sensitive details
Before We Start
There is a misunderstanding about Spring Security. it does not introduce new standards for security. It uses widely adopted security protocols and specifications. This makes it easier for developers to integrate security into their applications without having to build everything from scratch

For example, OAuth 2.0 is a well-known authorization protocol for securely application's resources without sharing user credentials. Instead of asking developers to create it from scratch, Spring Security provides OAuth Implementation with minimal configuration.
What Falls Under Spring Security?
All the following security specifications are implemented within Spring Security, making it easier for developers to integrate them into their applications:
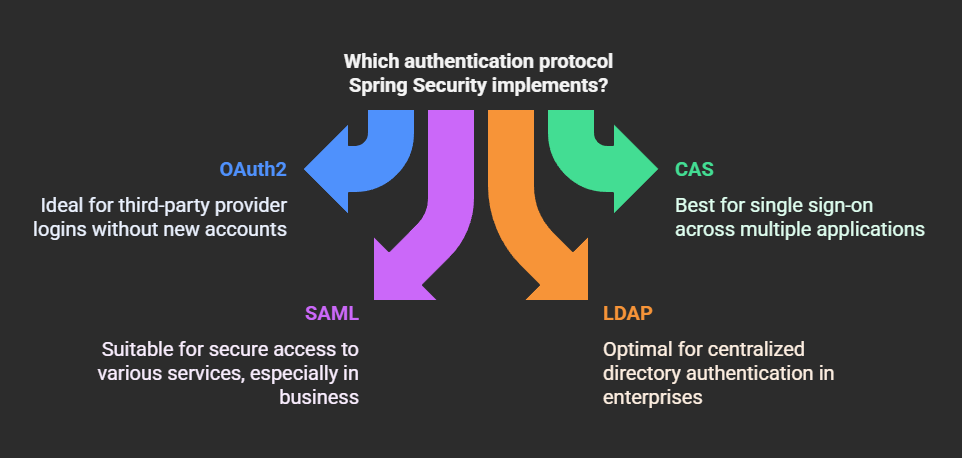
1.OAuth2
OAuth2 enables your application to support sign in with third-party providers such as Google, Facebook, and GitHub without having to create a new account.
Example: Whenever you see "Login with Google," it is using OAuth2.
2.CAS (Central Authentication Service)
CAS is an SSO authentication product that enables a user to log in to one application and then access several applications without continually logging in.

Example: Universities and companies use CAS to provide single sign-on there various products.
3.SAML (Security Assertion Markup Language)
SAML is another inter-organization authentication SSO protocol. It allows users to authenticate once and securely access a number of services.
Example: SAML is utilized by many business cloud applications such as Office 365.
4.LDAP (Lightweight Directory Access Protocol)
LDAP is used to authenticate users against a centralized directory, typically in enterprise applications.
Example: Many corporate networks use LDAP for employee logins. So all its employees are stored in LDAP and all its products integrate with LDAP to verify employee's credentials.
How Spring Security Works
Spring Security works by intercepting requests before they reach your application by using Filter Chain (It is a series of servlet filters that handle security logic before a request reaches the application) which enforces authentication and authorization rules to determine whether to grant or deny access.
The following is how it works in a step-by-step manner:
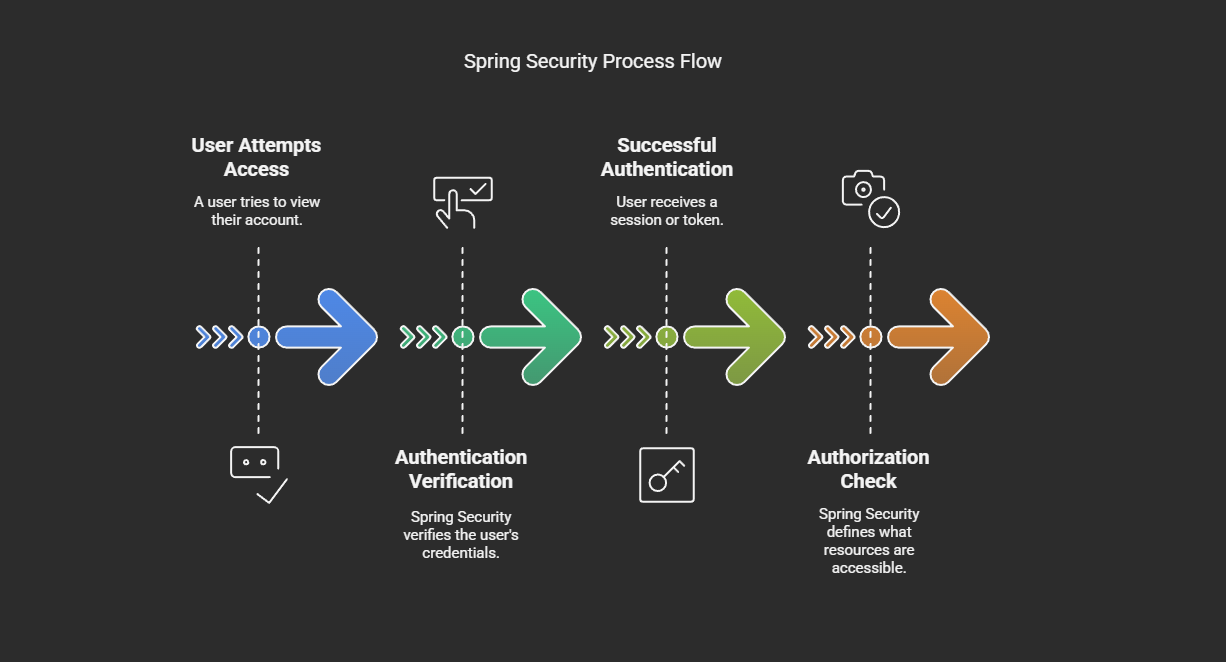
- A person attempts to view their account.
- Spring Security verifies their credentials (aka Authentication) against one the authentication protocols mentioned above or any custom one.
- On successful verification, the user is given a session or token. otherwise it redirects to the login page.
- Spring defines what resources they are allowed to access (aka Authorization).
Conclusion
Spring Security handles all these aspects, making security easy to manage.
Want to learn more?
👉 Read Next: What Is Filter Chain In Spring Security


